
Munin, Odin's own monitoring
Some people know Munin, the raven from northern mythology. It is in this case a distant cousin that you will discover in this article: Munin, the monitoring tool.

Summary
HTTPS is at the center of virtually all of our regular use of the global Internet. Facebook, Google, Amazon, Twitter, this blog and surely your favorite cooking-recipe website use HTTPS. In an ecosystem where even the most basic security measures are sometimes neglected, let's take a look at how to implement HTTPS on your own website and why you should do so.
This two-part article has a twofold objective: to raise awareness about the use of HTTPS (whether as a simple Internet user or as an administrator) and to show that its implementation is (no longer) intricated.
This first part will deal with the theory behind the HTTPS. What is HTTPS? Why use it and therefore why implement it?
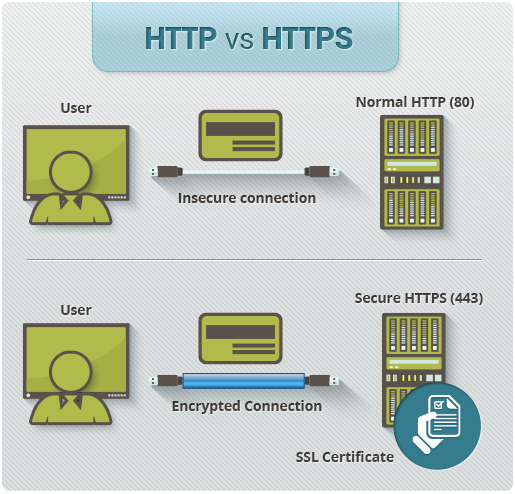
HTTP (HyperText Transfer Protocol) is the communication protocol used on the web to navigate, especially on websites accessible through your favorite browser. Thus, when you load a web page, the browser sends the request to the target server, which responds with the requested web page. All this is done in HTTP, and in the best case scenario, in HTTPS.
Without the secure - encrypted - layer of HTTPS, all communication is done "in clear", that is to say potentially readable or even modifiable by anyone between you (the client) and the server. HTTPS, by encrypting the communication through SSL/TLS, protects the data traveling through HTTP by making it understandable only to the recipient. To make sure that the recipient server is the one it claims to be, HTTPS authenticates the target with certificates, usually called "SSL Certificates".
As I said before, in simple HTTP all communications are transparent, therefore fully accessible to anyone between you and the server. Taking advantage of such a situation is called a "Man-in-the-middle" attack. Take a look at the diagram below:
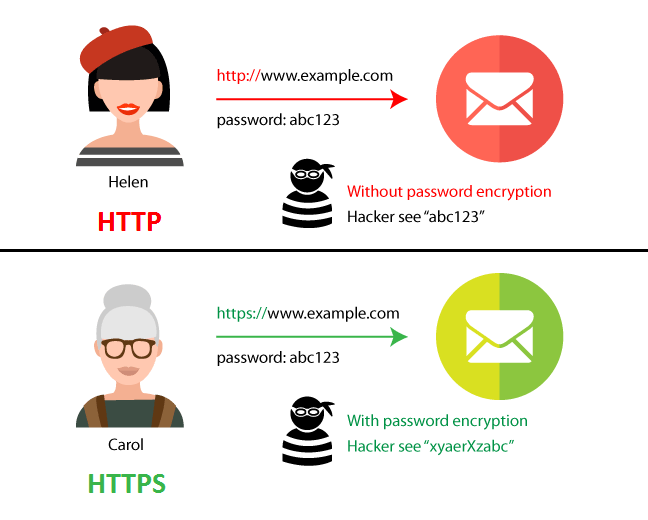
Here, Helen communicates with the website "http://www.example.com" in simple HTTP. Thus, the password she sent is fully visible to the attacker. Carol, visibly wiser or at least luckier, communicates with the site "https://www.example.com" in HTTPS. In this way, the attacker sees only the encrypted and therefore useless version of the password.
HTTPS also offers another protection, which is to make sure that the recipient is who they say they are and not an impostor. Thanks to certificates issued by recognized certification authorities (e.g. OVH, goDaddy, Amazon or Let's Encrypt), your browser is able to validate the identity of the site visited. This greatly helps to avoid man-in-the-middle attacks.
As an Internet user, only your vigilance will save you. If the sites you visit display the small green padlock at the URL level, then the site in question is validated by your browser. Of course, you must first trust your browser on its HTTPS management. But nowadays, all main browsers do this job perfectly and are regularly updated in this regard.
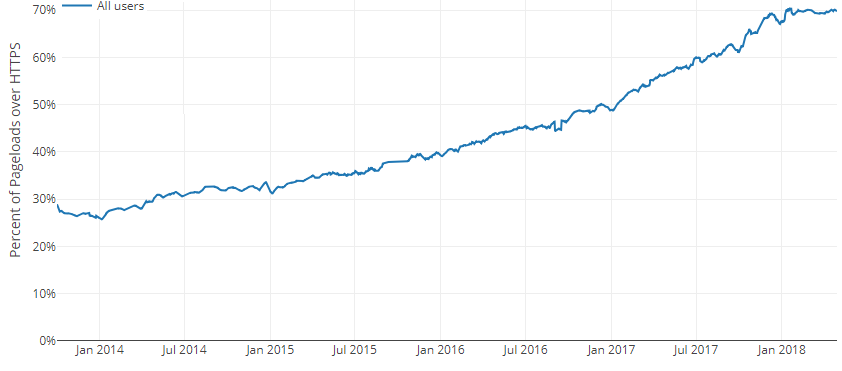
It is therefore up to the managers of the websites you visit to set up HTTPS. Today (as of August 2020 at least), about 80% of the websites visited are already encrypted according to Mozilla Firefox statistics (visible in particular on the page Let's Encrypt telemetry :
Today, setting up HTTPS on your own server is easy and completely free. So there is no excuse not to do it, as soon as you set up your site.
Let's Encrypt, in addition to providing certificates for free, provides a tool to retrieve and renew those certificates: Certbot. Simply clone the GitHub repository or go through their Docker image to retrieve via the terminal all the certificates you might need. Since March 2018, Let's Encrypt has been providing certificates called "wildcards", which will validate all your current and future subdomains via a single certificate. And this is always free of charge.
You should also be aware that simple HTTP sites are less well referenced by Google (since 2014) and that browsers clearly tend to signal to the user the lack of security of sites that are not certified and protected.
This first part on the theory around HTTPS is over: we have seen what exactly this protocol was, why it was important and how to use it, both as a web user browsing internet and as an administrator looking to secure his web platforms.
In the second part of this article, we will see how to technically implement HTTPS on a server, using mainly Let's Encrypt, Certbot, Nginx and Docker.
Author(s)
Jérémy Bernard
Mainly JavaScript and backend stuff.
You wanna know more about something in particular?
Let's plan a meeting!
Our experts answer all your questions.
Contact usDiscover other content about the same topic

Some people know Munin, the raven from northern mythology. It is in this case a distant cousin that you will discover in this article: Munin, the monitoring tool.

HTTPS, implementation with Docker, Certbot & Nginx.

DASH & HLS, two protocols to stream them all.